Theory vs. Practice
Diagnosis is not the end, but the beginning of practice.
The Artificially-Created Cyber-Chaos
The COVID-19 crisis would be seen in this respect as a small disturbance in comparison to a major cyberattack. We have to ask ourselves, in such a situation, how could we let this happen despite the fact we had all the information about the possibility and seriousness of a risk attack.
Did end-users get something valuable in return?
Or was it just (yet another) outright institutionalized fraud? (the taxpayer pays back the extravagant debt-financed government expenses).
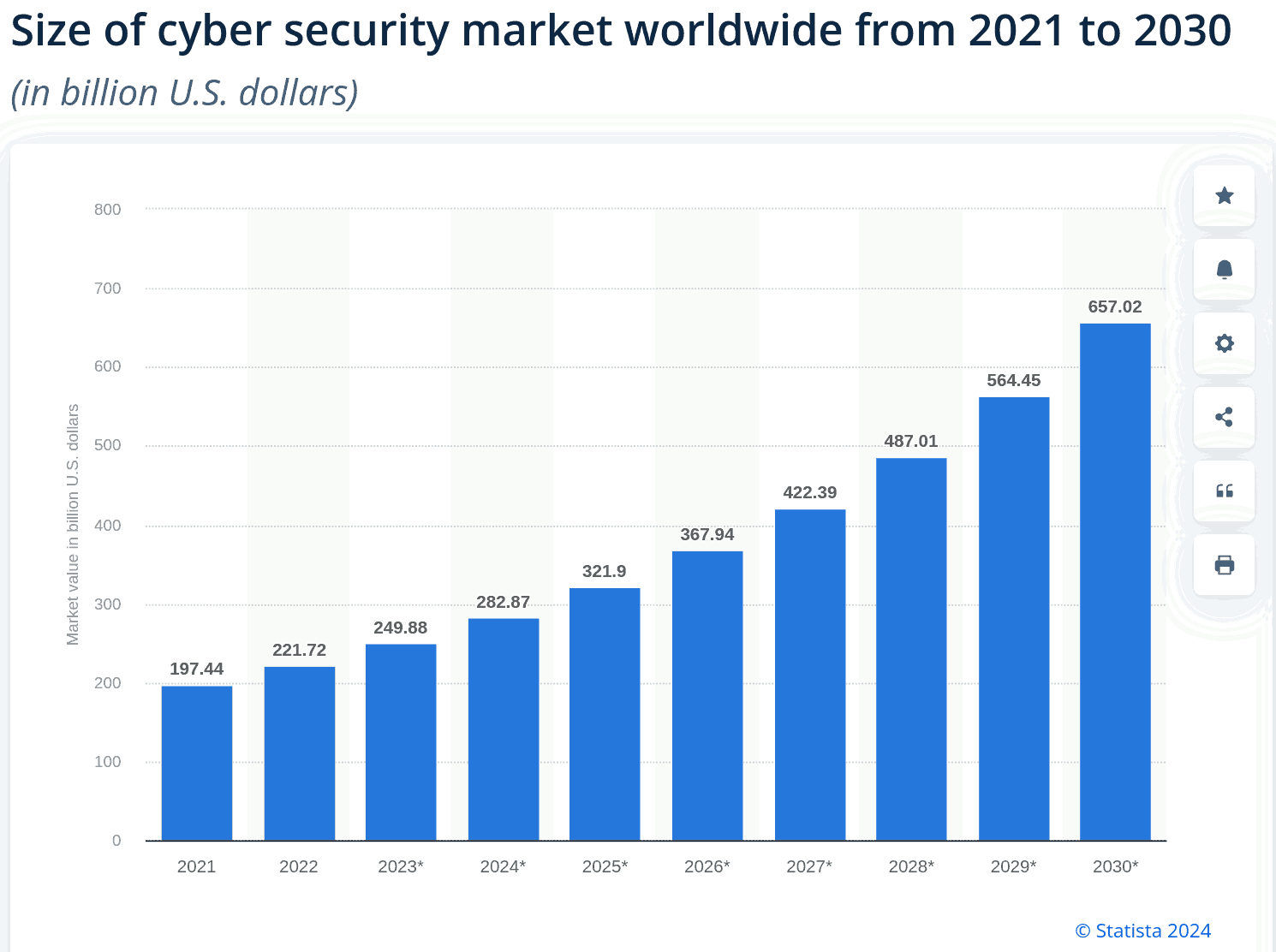
Tip: the industry expects the cyber-security market to more than triple within a decade – proof that this market is a fraud: the cost of the "protection" can only grow if this "protection" creates more problems than it solves.
Only the taxpayer has to suffer – because he is the only one paying the ever-growing bills.
The Problem
Since November 2022, the NSA recommends to use "memory-safe" programming languages because:
| } |
are "memory safety" issues (due to the OS memory allocator). |
Memory issues bypass encryption, intrusion detection systems, firewalls and even Security Operation Centers – making it pointless to waste this much money in ever-failing "security" tools – at least, as long as the elephant in the corridor is not addressed:
"New Flaws in TPM 2.0 Library Pose Threat to Billions of IoT and Enterprise Devices"
Here again, Out-Of-Bound (OOB) memory read/write accesses are the root cause of the vulnerability allowing arbitrary code execution in the TPM context (the organ supposedly protecting the device and OS).
The Solution
SLIMalloc (a memory allocator written in 2019 and first published in July 2020) makes C become a "memory safe" language:
Summary (5 pages):
http://twd.ag/archives/twd-slimalloc.html
2023 Technical Paper (36 pages):
https://www.researchgate.net/publication/367190325
(how it works, security and speed benchmarks with Facebook JEmalloc, Microsoft MImalloc and Google TCmalloc)
SLIMalloc proactively detects, blocks and reports the root causes of 70-90% of all past and future vulnerabilities (in operating systems, third-party libraries, and applications) – without overhead, false-positives or false-negatives (by running from within every single process).
"God, Make Me Pure, But Not Yet"
If designing and implementing SLIMalloc had been trivial, then this 50-year old problem would have been resolved a long time ago. Today's state-of-the-Art memory allocators, made by the richest companies in the history of capitalism, are all unsafe by-design.
Since $250 billion are spent every year to buy "cyber-security" products (and $657 billion planned for 2030), we must admit that either:
- creating SLIMalloc required more than what the OS (and security) vendors can deliver (in which case, in a "free and open market", all OS vendors and chip manufacturers should have swiftly and favorably responded to TWD's SLIMalloc licensing offers since 2020),
- cyber-security experts and vendors are crooks selling the feeling of improved security while doing little or nothing to achieve it (in which case, given the amount of public money robbed annually, several class actions are urgently required to stop this massive fraud – planned to tripple within the next decade),
- while BigCos get paid by governments for doing nothing useful, TWD, which addressed the root cause of the problem, was consistently excluded from all contracts and censored on major Web platforms (LinkedIn, Wikipedia – but not HandWiki.org – with search engines 'merely' avoiding to index the pages of TWD web sites that expose the GAFAM). "It's political" said an executive responsible for Cyber-Security at a major public organization.
or, since the major industry players declined TWD offers,
and, whatever the exact motivation of all players,
Fact: OS vendors make more money by selling unsafe products than they would by correcting "their vulnerabilities".
As a result, they will not do the right thing (serving their customers) as long as they have, in total impunity for decades, kept ransoming end-users by artificially ever-growing their surface of vulnerability.
Following SLIMalloc's publication, they have (a) excluded TWD, its child organizations and staff from LinkedIn and (b) published that: "We believe we have a strong competency in identifying work that is both high impact and efficiently achievable. Our aim is for funding entrusted to us to provide a strong return on investment in terms of making the Internet’s software infrastructure safer for everyone."
Few people enjoy being called crooks. But if they have a long history of criminal behaviors, to the point where they have been condemned many times decade after decade all over the world, how should they be called instead?
When crookery gets creative:
Among those inviting me to give them the source code for free by releasing SLIMalloc as an open-source project, I wonder how many would work 3 years of their life for me without getting any payment (because that's what they are asking me to do for them).
And, if, like they claim, "SLIMalloc is too strategic and important for the common-good to be kept proprietary", then, certainly, a small fraction of the $250 billion paid annually for inferior solutions should be diverted from other vendors and given to TWD.
This includes the OS vendors that sell vulnerable memory allocators since decades while knowing that it accounts for 60-90% of all "their vulnerabilities". If they were honest, and really trying to resolve today's cyber-security chaos, they would all have acquired a SLIMalloc license in 2020:
70% of the vulnerabilities addressed through a security update each year continue to be memory safety issues.
Apple's T2 Security Chip has an unfixable flaw allowing hackers to disable macOS security features and install malware.
A recent study found that 60-70% of vulnerabilities in [Apple] iOS and macOS are memory safety vulnerabilities. Microsoft estimates that 70% of all vulnerabilities in their products over the last decade have been memory safety issues. Google estimated that 90% of Android vulnerabilities are memory safety issues. An analysis of 0-days that were discovered being exploited in the wild found that more than 80% of the exploited vulnerabilities were memory safety issues.
Instead, hundreds of SLIMalloc weekly articles published on LinkedIn were censored because they demonstrated during three years that almost all the GAFAM vulnerabilities were automatically corrected by SLIMalloc.
Instead, SLIMalloc is censored from the Wikipedia "Memory Safety" page by several people including...
The DARPA (Defense Advanced Research Projects Agency) Program Manager, Defense and GAFAM contractor, and CTO of TrailOfBits.com William Woodruff has demonstrated a passion for eradicating SLIMalloc from Wikipedia... that is, only when he believes that he is safely hidden behind several fake Wikipedia accounts in an attempt to preserve his anonymity.
The problem with backdoors is that they are a two-edged sword. And, to quote an expert in the matter:
If you have something that you don't want anyone to know, maybe you shouldn't be doing it in the first place.

Subject: Your Censorship of SLIMalloc on Wikipedia
Date: Wed, 26 Apr 2023 08:29:15 +0200
From: P. Gauthier
To: William Woodruff <william@yossarian.net>
Dear Mr. William Woodruff,
Since you are "Engineering Director, R&D practice" at TrailOfBits.com "Responsible for directing the Ecosystem Security group",
and "Program manager and technical lead for program analysis research across DARPA programs" for Cyber-Security,
and have yourself given "courses on ethical hacking" and contributed to "security tooling",
it is surprising to see you repeatedly censoring SLIMalloc on Wikipedia under the fallacious accusation of "Vandalism",
especially since all the other commercial products listed on this Wikipedia page are immensely inferior to SLIMalloc - both on capacity and performance.
We would be delighted to publish SLIMalloc as "Open Source" software - if only we were sponsored or funded - either by private investors or by the taxpayer.
In the absence of funding, we have to keep trade secrets private so that we can sell our works and make a living.
I am open to any discussion or suggestion you might have.
Sincerely,
Pierre Gauthier, CEO
Tel +41 55 414-2093
http://twd.ag
William Woodruff never replied to my email – and doubled-down the censorship (hence my disclosure of his real identity hidden behind several account nicknames)... while reverting to block, at least during 15 days (again, under a fake account: "Widr" = "William" + "Woodruff") the publication of SLIMalloc under the pretext that this is "disrupting editing" (like if restoring a censored without any argument ResearchGate paper is not a valuable contribution to Wikipedia):
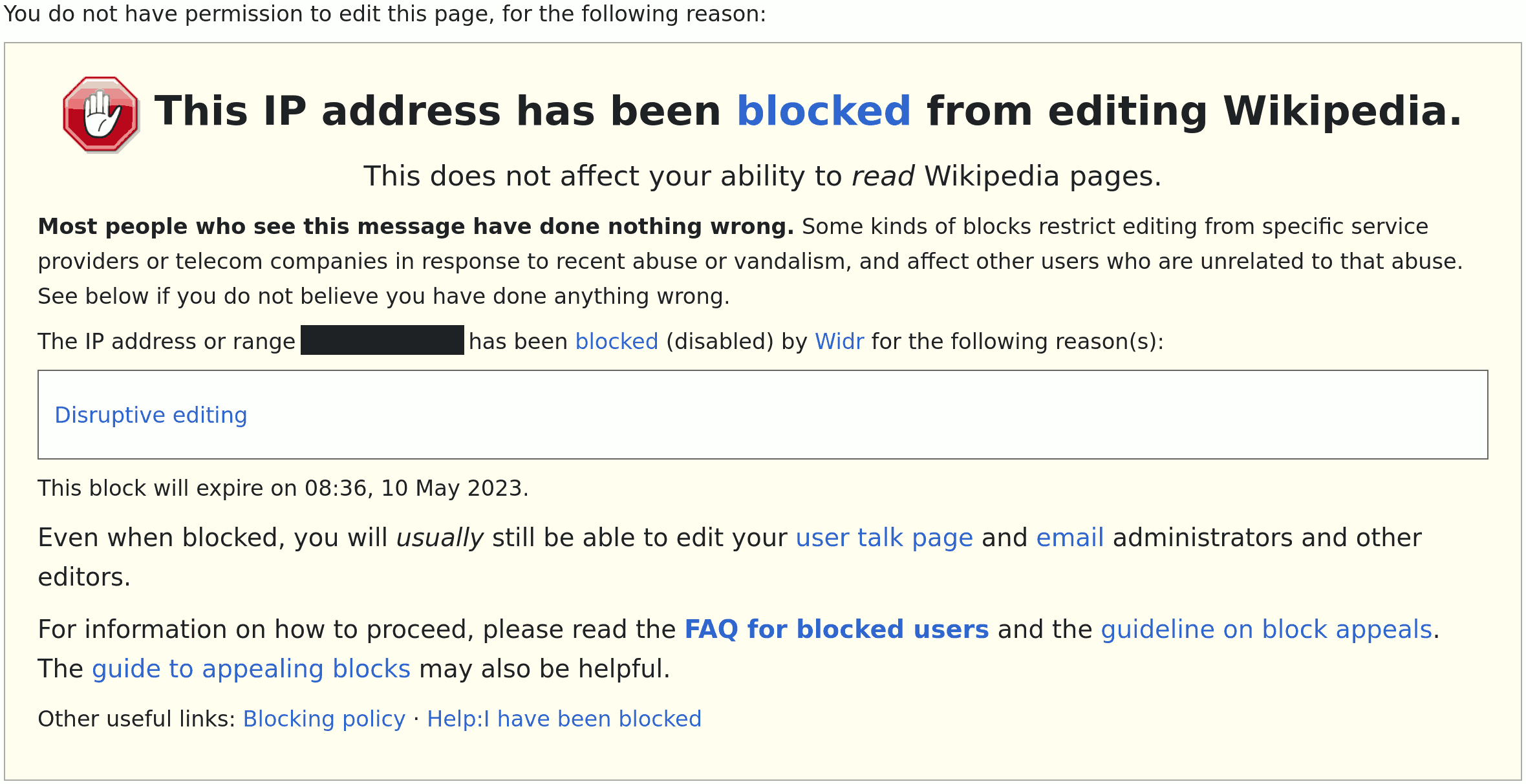
William Woodruff also used supervisor Wikipedia privileges to modify the edition journal history of the Wikipedia "Memory Safety" page in an attempt to hide his identity after his fake accounts had been traced to one single person, him (presumaby, to avoid sanctions and to avoid being ashamed by seeing his illegal activities being exposed publicly).
The original version, disclosing the saboteur's identity:
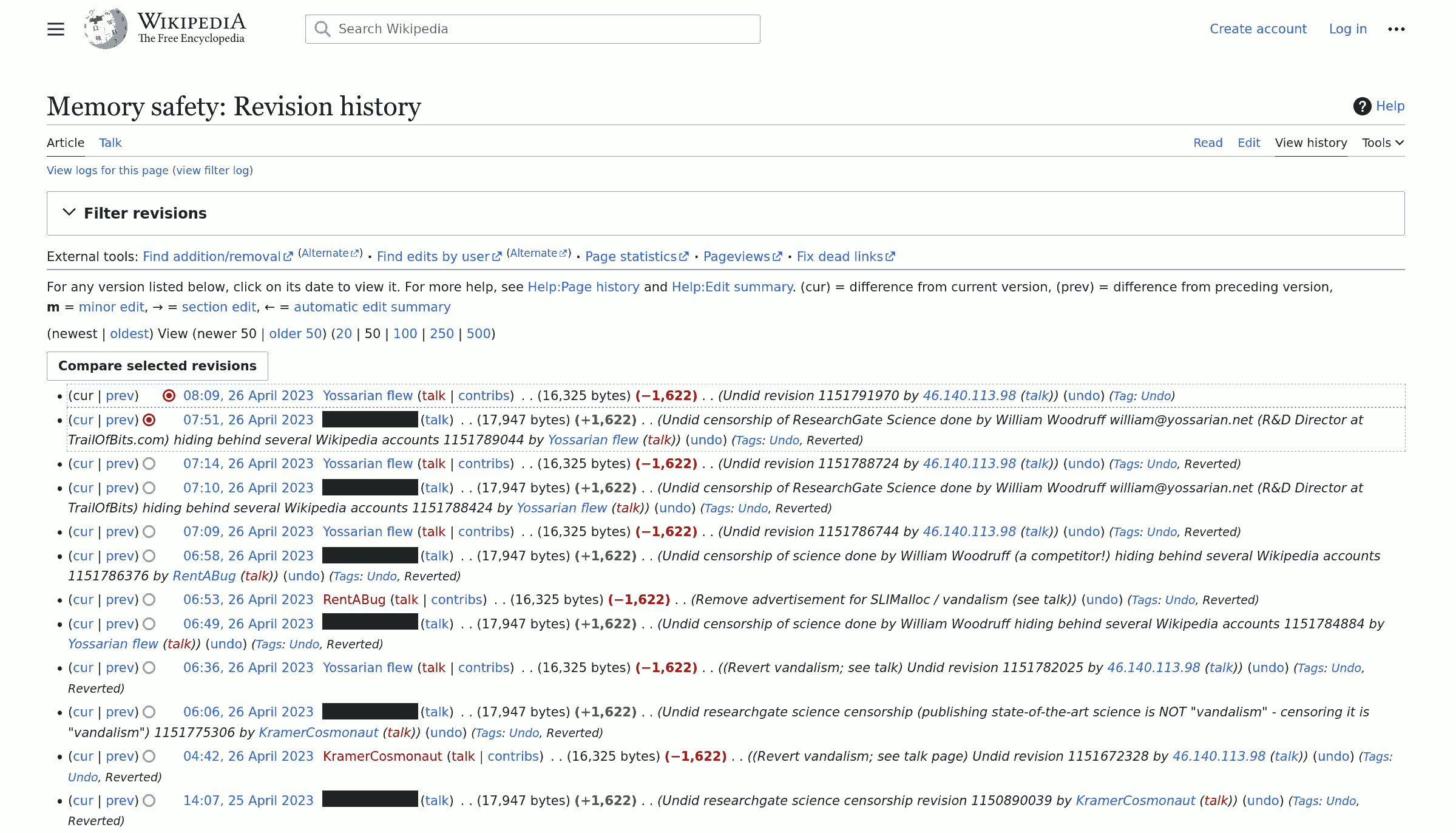
The 'cleaned-up' version (the saboteur rewriting history to censor his uncovered identity):
_2023-05-03-at-08-28-47.png)
A Wikipedia Editor anonymously justifies the censorship of SLIMalloc by claiming that C/C++ Memory-Safety is "impossible to achieve"... and therefore that anyone pretending to resolve the problem is necessarily "incompetent".
It seems that they did not read the "Memory-Safety" page they are censoring: it lists (like the Slimalloc paper) 4 other tools trying to make C memory-safe, with GOOGLE's LLVM-ASAN (crippled by gazillions of false-positives and aborting each time a process with corrupt memory) being just 2x slower than SLIMalloc which blocks upfront and documents violations without ever stopping programs):
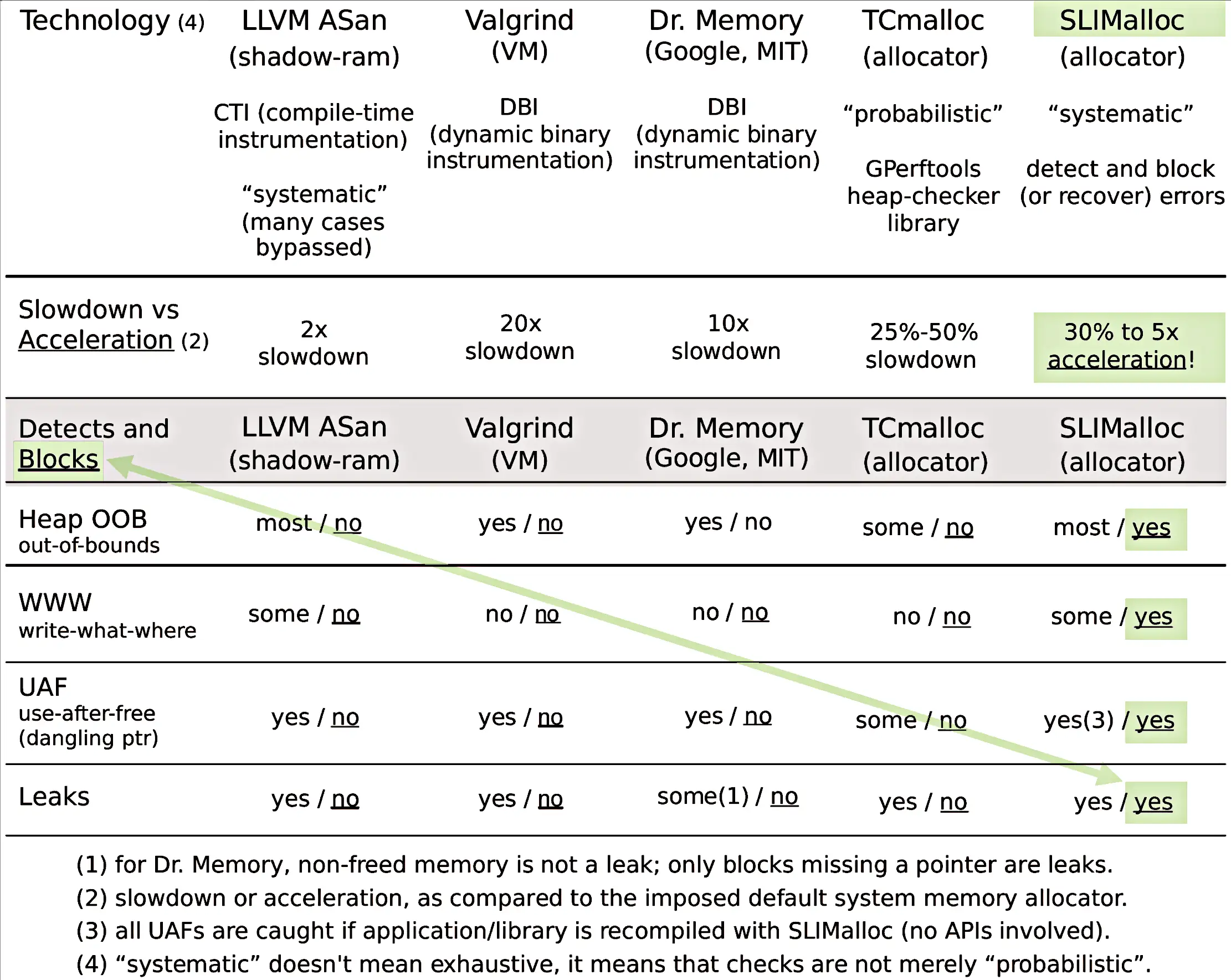
So, the real problem seems to be that it is unacceptable for the Wikipedia Editors that anyone can do so much better than GOOGLE's LLVM-ASAN which is 2x slower than GlibC (while SLIMalloc is 30%-5x faster than GLibC – despite having many more features, as documented in the censored paper with many benchmarks written by MICROSOFT, INTEL and IBM involved in tens of thousands of systematically-metered, documented test runs over a period of time lasting more than 10 hours).
The censorship comes from the CTO of TrailofBits.com which, with a staff of more than 60, presents itself as a "top-of-the-line" Cyber-Defense contractor:
"Since 2012, Trail of Bits has helped secure some of the world's most targeted organizations and devices. We combine high-end security research with a real-world attacker mentality to reduce risk and fortify code.
We help our clientele – ranging from Facebook to DARPA – lead their industries. Their dedicated security teams come to us for our foundational tools and deep expertise in reverse engineering, cryptography, virtualization, malware, and software exploits. According to their needs, we may audit their products or networks, consult on modifications necessary for a secure deployment, or develop the features that close their security gaps.
We believe the most meaningful security gains hide at the intersection of human intellect and computational power.
As a cybersecurity research and consulting firm, we serve clients in the defense, tech, finance, and blockchain industries. Our teams help with their most difficult security challenges by designing and building new technology, researching new techniques to advance the state of practice, and reviewing the security of the latest available technology products before they hit the market."
So, it seems that these honorable professionals (TrailofBits.com and their customers – the U.S. DoD and the GAFAM) did not like SLIMalloc (2020) because, even in 2023, they are still unable (and/or unwilling) to deliver any capacity at that level of expertise and usefulness.
Oscar Wilde (1854-1900) wrote that "Imitation is the sincerest form of flattery that mediocrity can pay to greatness" but, obviously, covert sabotage and censorship are an even more sincere homage.
If TrailofBits.com endorses his Director of R&D's (illegal) sabotage that's unfair anti-competitive practice – possibly involving TrailofBits.com clients. Not glorious for a Cyber-Security "leader" helping Tech "leaders" (among which Facebook, author of the JEmalloc memory allocator that did not compare favorably to SLIMalloc in our censored paper).
This also demonstrates that Wikipedia (1) is not "open to the public" for edition (2) grants complete editing privileges to people acting like criminals (censoring their competitors), privileges that are then (3) used by the U.S. intelligence community against foreign commercial companies –for immediate private economic gains (like selling backdoors to governments and exploiting them for personal reasons) – yet another problem addressed by international laws (hence the wrongdoers seeking anonymity via fake editor and supervisor accounts to rewrite history and block more competent market players).
William Woodruff has a personal website at yossarian.net (a domain registered in 2017 at the GOOGLE registrar) which explains in great details who William thinks he is, in his own words):
"i am not naturally talented at math, but have always been fascinated by logic and language. that fascination drives my current interests: compilers and program analysis, systems programming, and cybersecurity.
i believe strongly in software engineering: i like writing correct and reliable software, especially for other programmers. i think that security engineering and quality engineering are the same thing.
ethical philosophy appeals to me most of all. in particular, i am interested in theories of rights and duties, as well as the problems of coercion and exploitation as they concern and (de)legitimize choice. i am also interested in moral education as it applies to beneficence, charity and authenticity (of the good/bad faith kind), and public discourse."
When you read that William Woodruff is so concerned by ethics, quality programming and, in particular, cyber-security – the very values promoted in real-life by the censored 36-page SLIMalloc ResearchGate publication – you may wonder why William Woodruff is at war against SLIMalloc and feels the urge to censor it on Wikipedia by calling it "Advertising" and "Vandalism".
Despite his contempt for capital letters, William Woodruff should consult a dictionary (and try to apply to self what he professes):
Ethical: "in accordance with the accepted principles of right and wrong that govern the conduct of a profession. Synonym: moral."
Moral: "concerned with the judgment of right or wrong of human action and character. Teaching or exhibiting goodness or correctness of character and behavior. Conforming to standards of what is right or just in behavior; virtuous."
The choice of the nickname "Yossarian Flew" is also revealing: in a satirical 1961 novel "Capt. John Yossarian" is a 28-year-old captain in the 256th Squadron of the U.S. Army Air Forces where he serves as a B-25 bombardier, who "unlike many of the other soldiers, tries to escape the realities of war by getting drunk, gorging himself in the mess hall and having sex" – and "plots an emergency heading into Switzerland so he can be interned for the duration of the war under conditions of utmost ease and luxury".
Thirty years ago, at least in computer-science, the USA were able to win without cheating. This time is over. When the staff in charge of your Department of Defense's (DoD) R&D public-money spending is too young, too incompetent, and shamelessly proud to betray the taxpayer, this has consequences: you show who you are and everyone will look for business and supply elsewhere.
This might prove difficult: for example, SLIMalloc was automatically been imported by HandWiki.org which prominently promises not to ever apply consorship... yet SLIMalloc has been censored there too (it only took some more time).
Moral of the story: don't support Treacherous Computing, support the Righteous alternatives (or create ones when there are none)!
Is open-source an opportunity for developers and end-users – or only for funded BigCos?
Since 2020, all invitations to open-source SLIMalloc have lacked any form of compensation. When expressed, the promise was that, after SLIMalloc would be publicly made available for free, then, "most probably, TWD would later get recognition and make a fortune out of it".
If fancy cars were easier to sell after they were first given for free to every single driver, then everybody would enjoy hot wheels.
It did not happen because car manufacturers would be broke far before the market is saturated by free cars.
Why then using such a fallacy to get SLIMalloc for free if that's not to steal (and then sabotage it)?
There's also this recurring claim that open-source is safer because many people can check the code. Proof that this is not the case: all OS vendors (open-source and proprietary) market the same decades-old backdoor using flawed memory-allocator designs.
Yet, these OS/Chip vendors have all the money they need to acquire and promote valuable contributions:
- with a net worth of $150 million, Linus Torvalds receives an annual salary of $10 million from the Linux Foundation.
- IBM has acquired Red Hat (a Linux vendor) for $34 Billion.
- The World's Largest Tech Companies In 2022:
Rank Name Country Sales Market Value "World's Best" Memory Allocator ---- ------------------ ----------- --------------- --------------- ------------------------------- 1 Apple Inc. USA $378.7 billion $2.6 trillion 2 Alphabet Inc. USA $257.5 billion $1.6 trillion TCmalloc (unsafe by-design) 3 Microsoft Corp. USA $184.9 billion $2.1 trillion MIMalloc (unsafe by-design) 4 Samsung Group South Korea $244.2 billion $367.3 billion 5 Tencent Holdings China $86.9 billion $414.3 billion 6 Meta Platforms USA $117.9 billion $499.9 billion JEmalloc (unsafe by-design) 7 Intel Corp. USA $79.0 billion $190.3 billion 8 TSMC Taiwan $61.5 billion $494.6 billion 9 Cisco Systems Inc. USA $51.5 billion $213.4 billion 10 IBM USA $67.3 billion $124.3 billion(Source: Forbes' Global 2022)
So, SLIMalloc (made by TWD, a company founded in 1998 and that has never received extern funding) outdoes in performance and security since its first release in 2020 the (autoproclaimed) "World's Best" memory allocators made by companies that cumulate USD 4.2 trillion of "market value" (and hundreds of thousands of engineers).
TWD did so every single time it has made a product public, see the last page of this SLIMalloc 5-page leaflet, and every time the "market leaders" reverted to illegal anti-competitive practices (self-complacency is not the best way to demonstrate one's legitimacy, and its damages invariably cause degenerescence and even more treachery to the point where everything crumbles under the weight of its own sins – remember, "the higher the pedestal, the harder the fall").
Some will depict this rant as an exaggeration but in fact it reflects a very sick industry and twisted markets abusing State powers to promote their interests at the expenses of everyone else. And it seems that for many people, SLIMalloc (a game-changer innovation that both VCs and industry leaders want – but only if it is given for free) is not an isolated case:
Fairness or Robbery?
"You should never open source anything that has a core value to your business. If there is a trade secret – an idea or a way of its implementation that makes your business unique, you should not open source it so that it does not become available for your competitors. Yet, if you have ideas and tools that can be used by the public without any loss for your business – open source them."
FreeCodeCamp.org
Fairness or Robbery?
"Cloud vendors use numerous open-source projects that they did not create, but run as-a-service. These provide Cloud vendors with billions of dollars of revenue per year. To be clear, this is not illegal. But it is not conducive to sustainable open-source communities, and especially commercial open-source innovation."
TechCrunch.com
Fairness or Robbery?
"Here in Stack Exchange we have mentioned some cases of lawsuits involving open source projects that allegedly breached patents and were sued. I'm curious, however, in the opposite case: has anyone been sued for not following the terms of an open source software that has been used?"
StackExchange.com
Fairness or Robbery?
"Most people don’t realize it, but many of the devices and apps you use every day are built on top of open source software, maintained by one or two developers that aren’t paid for their time, who patch bugs and improve their code to give back to the community or as a passion project."
TechCrunch.com
Fairness or Robbery?
"Open-source developers say Big Tech profits off their software while contributing little back. Now as burnout ushers in a breaking point, some say companies should provide code, bug fixes, and even salaries to keep the digital ecosystem afloat."
BusinessInsider.com
Fairness or Robbery?
"Relying on volunteers to maintain every open source project isn't long term sustainable. Funding open source projects could keep development moving, but would that funding be raised and who would pay for it?."
StackOverflow.blog
Open-Source Many-Eyes Safety?
"You can't trust code that you did not totally create yourself. No amount of source-level
verification or scrutiny will protect you from using untrusted code."
Ken Thomson, 1984 Turing Award
(Note: all OS vendors deploy memory allocators based on the same flawed design that is an obvious 50-year old backdoor)
Open-Source Many-Eyes Safety?
"There is a view that because open source software is subject to review by many eyes, all the bugs will be ironed out of it. This is a myth."
OpenSource.com
Open-Source Many-Eyes Safety?
"On average, good open source is about as good as good proprietary, and about as bad as bad proprietary."
ZdNet.com
Open-Source Many-Eyes Safety?
"Many people have access to the source code of open source software, but not all of them have good intentions. While a lot of people utilize their access to spot defects and make improvements to the program, others use this privilege to exploit the product’s vulnerabilities and create bugs that can infect hardware, steal identities or just annoy other users."
ConnectUsFund.org
Open-Source Many-Eyes Safety?
"Security researcher exposes malicious GitHub repositories that host more than 300 backdoored apps."
PacktPub.com
Open-Source Many-Eyes Safety?
"Open source developer corrupts widely-used libraries, affecting tons of projects."
TheVerge.com